The PHOENIX Project Achievements Summary
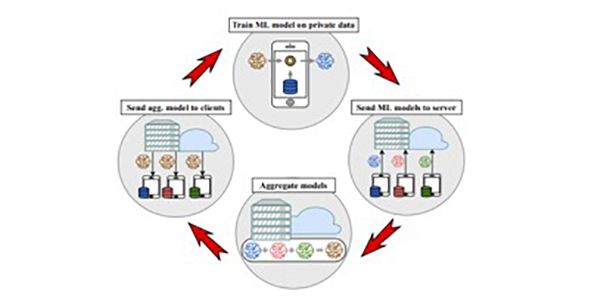
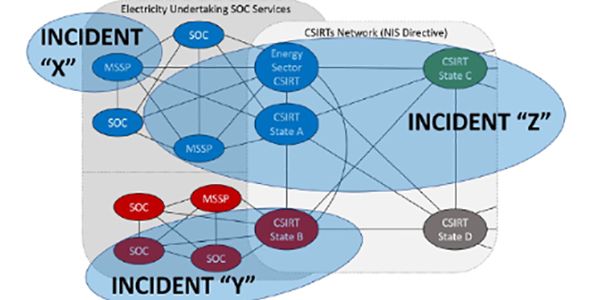
Being at the end of the PHOENIX project, we would like to distinguish its biggest results, achieved with the cooperation of various partners, representing different environments. Overall the project has progressed very well and is on track with expectations, whereas the achievements have been implemented and demonstrated.