Compliance of PHOENIX Incidents Information Sharing Platform with NCCS and Cyber Resilience Act
Recent developments in the EC cybersecurity policy and regulatory landscape have been noted with the introduction of the Network Code for Cybersecurity aspects of Cross-border Electricity Flows (NCCS) [1] and the Cyber Resilience Act (CRA) [2].
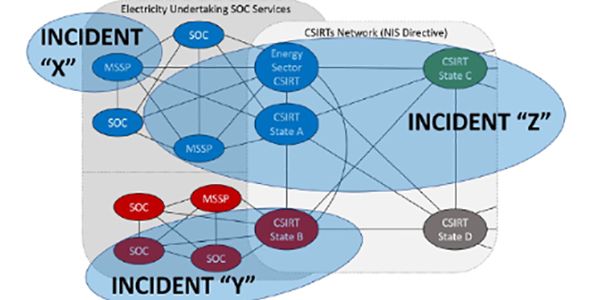
NCCS establishes a network code, which lays down energy sector-specific rules for cybersecurity aspects of cross-border electricity flows, including rules on common minimum cybersecurity requirements, planning, monitoring, reporting and crisis management. Key recommendations include: i) a cross-border risk assessment and management approach, ii) common functional and non-functional security controls and requirements definition, iii) information sharing among all involved stakeholders in a highly trusted environment, as depicted in the following figure, derived from the specification of NCCS1.
CRA aims to ensure that cybersecurity is incorporated in the implementation life cycle of products and services by design and also to safeguard that the products and services that are delivered provide advanced cybersecurity by default.
The effect of these developments to the ongoing cybersecurity platforms, such as the Incidents Information Sharing Platform (I2SP) resulting from the H2020 PHOENIX Project, that envisage to protect (critical) infrastructures are definitely positive and welcomed.
In the first place, NCCS suggests that in order to enable closed and trusted interactions between grid participants, they will have to be integrated in an all-embracing communication scheme, where a dedicated “European trusted Energy CSIRT” is implemented for gathering, evaluating and distributing the energy-sector specific information. This CSIRT will be the trusted hub connected to grid participants by the means of a national CSIRT or by a sector specific CSIRT to gather the mandatory reporting flow (according to the NIS Directive). But it will also be directly connected to grid participants to ensure a timely distribution of information and enable a voluntary information sharing stream among grid participants. It should operate at EU-Level to process all the necessary information and data, and make sure that information is being properly sanitized, stored as anonymized (or pseudonymized) data, and shared within the trusted community of grid participants. Grid participants that provide the data are also the data owners and should decide what detail of information is shared within the trusted community, and if it can be released outside of this trusted community after a period of time. This principle creates trust and facilitates voluntary information sharing within the community of grid participants.
In that respect, I2SP is significantly aligned with the cybersecurity information sharing principles within trusted communities of stakeholders enabling secure interactions and allowing control of what is shared to whom and under which contexts and terms. It has defined and implemented the notion of Trusted Circles (TC), adopted by the MeliCERTes [3], that indicates a group of organizations that are eligible and interested to contribute CTI information, collaborate and get benefited by the analysis conducted by the I2SP and the enriched CTI information that it effectively provides in return. The participating organizations, in order to form a TC, have to share some common incentives. Indicatively, TC members share a common geographical, regulatory or domain specific correlation, responsibility and/or interest. The participating organizations should provide their consensus in order to participate in a Trusted Circle. Ultimately, the formation of a TC facilitates the definition and enforcement of the sharing policy (Sharing Manifest) that dictates and drives each information sharing activity among the I2SP eligible participants. We are considering a TC as a conscious decision made by an organization (EPES) to share Cybersecurity Threat Intelligence information, produced by I2SP, concerning itself with its TC members, in an effort to alert them and raise their security awareness and subsequently preparedness regarding ongoing or near future security incidents at national, cross-border and Pan-European level. The participating EPES entities that are interested or obliged by law to receive the shared security incident information, will need to express their interest and formally register to I2SP for enabling the exchange of CTI information. Thus, we have constructed an Information Sharing Manifest that captures all the necessary data for forming and joining a Trusted Circle, but also for joining the I2SP framework.
In addition, I2SP is totally aligned with the suggestions of NCCS, addressing the risk assessment requirement not only at regional level, but also at national and cross-border contexts, while further entailing cybersecurity incident and crisis management tasks such as coordination and collaboration activities, mitigations actions identification and recommendation.
From the point of view of the I2SP, CRA would indirectly strengthen the suggested platform by strengthening the cybersecurity of digital products and ancillary services that the I2SP aims to protect. The initiative could also lead to the replacement of legacy products, components and services, which are not only less secure but also less energy-efficient and environmental-friendly.
Finally, it is worth stressing that the I2SP development life cycle has strongly adhered to security by design principles. This is translated on the one hand to the utilization of state-of-the-art secure and privacy preserving communication channels that have driven the information propagation both internally (within I2SP) and externally (towards the eligible participants) and on the other hand, to the adoption of end-to-end security development practices pertaining to a DevSecOps approach, that has practiced advanced security hardening throughout its entire software development lifecycle.
We have been closely monitoring the advancements on the policy and regulation cybersecurity landscape to ensure compliance and thus subsequent acceptance and faster adoption of I2SP by the target stakeholders.
[1] Network Code for Cybersecurity aspects of cross-border electricity flows, 14 January 2022 [Online]. Available at: https://eepublicdownloads.entsoe.eu/clean-documents/Network%20codes%20documents/NC%20CS/220114_NCCS_Legal_Text.pdf
[2] Cyber Resilience Act, 15 September 2022 [Online]. Available at: https://digital-strategy.ec.europa.eu/en/library/cyber-resilience-act
[3] MeliCERTes CSP, “The Cyber Security Platform MeliCERTes,” [Online]. Available: https://github.com/melicertes












