Secure exchange of cyber threat intelligence using TAXII and DLTs

Critical Infrastructures (CI) may be defined as collections of cyber-physical systems whose disruptions or failures result in destructive financial and health consequences for large population segments. Electrical Power and Energy Systems (EPES) constitute some of the most essential critical infrastructures, particularly due to the high dependency of other technologies, services as well as CIs on the proper operation and availability of power networks.
The introduction of Information and Communication Technology (ICT) in the operational processes of modern EPES, although of great importance, introduces new risks to the operation of EPES, in the form of cyberattacks targeting the energy networks. Under this perspective, EPES protection against cyberattacks has drawn significant attention in the literature. To combat adversaries, conventional information security technologies such as Intrusion Detection Systems (IDS) have emerged as integral parts of the operations of EPES, they are, however, unable to secure EPES infrastructure against advanced/complex cyberattacks.
Recent studies [1, 2] tackling modern cyber-security challenges in the energy sector collectively highlight the need for highly scalable and secure cyber-security information sharing platforms (CIS). At the same time, sector-specific Information Sharing and Analysis Centres (ISACs) such as European Energy–Information Sharing and Analysis Centre (EE-ISAC) and the Electricity Information Sharing and Analysis Center (E-ISAC) have been recently formed to establish trustworthy connections between governmental institutions and relevant industry actors including vendors and utilities and also to enable reliable sharing of Cyber Threat Information (CTI) towards accelerating detection and mitigation of cyberattacks.
The PHOENIX Project is mainly focus on protecting European EPES infrastructures against cyber attacks caused by malicious activities. To achieve this, PHOENIX offers a cyber-shield armour to European EPES where cyber security incidents and attack patterns can be recorded and shared securely among responsible parties and can be subsequently used for prevention, early detection and mitigation of cyber attacks. Despite the definite need for CTI data exchange, little work has been conducted towards standardizing the means of achieving this exchange securely and efficiently. One of the most prominent and widely used frameworks towards that direction is the adoption of the Structured Threat Information eXpression (STIX) data model in combination with Trusted Automated eXchange of Indicator Information TAXIITM framework. The latter, however, presents major deficiencies with regards to i) authenticity and non-repudiation auditing of data and ii) suitability for event-driven architectures and real-time applications, even though the protocol already considers relevant operation modes.
In PHOENIX platform, Secure and Persistent Communication (SPC) layer presents a novel approach towards enabling secure and real-time exchange of CTI data related to the security status of EPES infrastructures, by extending the technological capacity of the TAXII framework, hence addressing the previously identified deficiencies by properly integrating Distributed Ledger Technologies (DLT) and a generalized publish-subscribe middleware, respectively.
Figure 1 depicts the overall architecture of the proposed solution which comprises three main components: TAXII client, Medallion node (i.e. TAXII server) and publish/subscribe middleware. The TAXII framework expansion gives the ability to CTI producer and consumer t o confirm that threat information has not been modified. Additionally, the generalized publish-subscribe middleware creates an opportunity for real-time and scalable sharing of CTI data between different components and services.
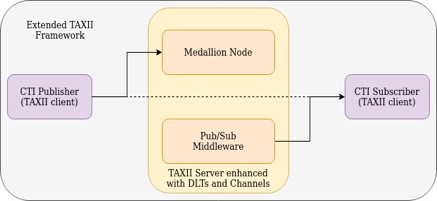
The TAXII server stores CTI data received from various clients in its database. This mechanism, however, does not guarantee the authenticity of STIX objects maintained by the TAXII server. To address this deficiency, TAXII server is extended to use a private permissioned DLT namely Quorum as an immutable data storage to ensure the integrity of CTI data records in its database. To this end, the hash of every STIX object is written in Quorum ledgers since the CTI data generated by EPES components might explicitly or implicitly contain personal data thus storing them in ledgers may lead to violation of the GDPR right to be forgotten due to the immutable nature of DLTs. The TAXII server also passes the CTI data to the pub/sub middleware where STIX objects are forwarded to pre-defined channels. On the other hand, the TAXII server upon reception of a query for specific CTI data retrieves the related STIX objects from its database as well as respective hashes from the ledgers. Further, it compares each hash object with the hash of the actual STIX object provided by its database. The identical hashes imply that the data record in the database is valid while the discrepancy in the hashes indicates some modification in the data record. In the latter case, the TAXII server labels the STIX record as an invalid entry [3].
The initial prototype of the proposed solution was developed and presented successfully in the mid-term review meeting of PHOENIX project in June 2021 as a means to verify its applicability in terms of reliability and scalability.
References:
[1] Ivo Friedberg, Florian Skopik, Giuseppe Settanni, and Roman Fiedler. Combating advanced persistent threats: From network event correlation to incident detection. Computers & Security 48 (2015), 35–57.
[2] Mirco Marchetti, Fabio Pierazzi, Michele Colajanni, and Alessandro Guido. Analysis of high volumes of network traffic for advanced persistent threat detection. Computer Networks 109 (2016), 127–141.
[3] Maryam Pahlevan, Artemis Voulkidis and Terpsichori-Helen Velivassak. 2021. Secure exchange of cyber threat intelligence using TAXII and distributed ledger technologies – application for electrical power and energy system, In second International Workshop on Electrical Power and Energy Systems Safety, Security and Resilience












