Pan-European Incidents Information to Sharing Platform (I2SP) Machine Learning on Attack Data

Attack trees have been widely recognized as a systematic method for specifying system security based on vulnerabilities. The nodes of the tree represent the different stages of an attack, while the root node represents the attacker’s main goal: to impair the normal functionality of the system.
The PHOENIX Pan-European Incidents Information to Sharing Platform (I2SP) receives a continuous stream of cybersecurity attacks coming from various EPES across Europe, and implicitly translates these series of attacks into pan-European attack trees. These high volume and velocity time-series data are then processed and further analyzed using beyond the state-of-the-art Machine Learning (ML)/ Deep Learning (DL) algorithms.
Attack trees have been widely recognized as a systematic method for specifying system security based on vulnerabilities. They facilitate in organizing intrusion scenarios by (i) identifying vulnerabilities, and by (ii) analysing the weak points and dependencies among the vulnerabilities, representing these dependencies in the form of an AND-OR tree. An attack tree is developed for each asset that could potentially be attacked. The nodes of the tree represent the different stages of an attack, while the root node represents the attacker’s main goal: to impair the normal functionality of the system. Additionally, the interior nodes (i.e. also including the leaf nodes), represent possible system states during the execution of an attack, illustrating the level of compromise (e.g. acquisition of root privileges, etc.), alterations to the system configuration (e.g., modification of trust or access control), and state changes to specific system components (e.g., placement of certain types of malwares). The branches of an attack tree represent change of states caused by one or more actions taken by the attacker.
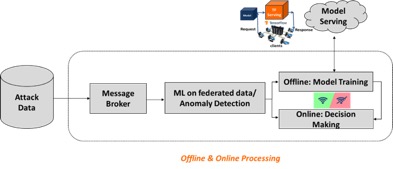
The PHOENIX Pan-European Incidents Information to Sharing Platform (I2SP) receives a continuous stream of cybersecurity attacks coming from various EPES across Europe, and implicitly translates these series of attacks into pan-European attack trees. These high volume and velocity time-series data are then processed and further analyzed using beyond the state-of-the-art Machine Learning (ML)/ Deep Learning (DL) algorithms, with main goals: (i) the detection of abnormal patterns that reveal the existence of coordinated attacks, and (ii) the identification of cascading effects on the received Cyber Threat Intelligence (CTI) data. The ML/ DL framework that is designed and developed for this purpose, predicts the exact location (i.e., the next node of the attack tree) for which exists high possibility of having an attack at a greater level (i.e., national), that indicates the existence of a coordinated attack. Specifically, we solve a multi-class and multi-output time-series classification problem that is separated into two distinct phases, the offline, that represents the model training process, and the online, that corresponds to the decision making and does not involve model re-training. During the offline training stage, we store the learnt models, to be able to distribute them for the decision-making stage. The outcomes of the ML process are then visualized on the I2SP dashboard on a user-friendly, STIX-compliant format. The following figure illustrates the main diagram of the proposed application, including the individual steps of the ML analysis.