Malware: If they are down, you can be down too
[9 of May 2021] In the news today; Alpharetta, Georgia-based Colonial Pipeline has been (successfully) targeted and taken down by a Ransomware attack, threating the transportation of 2.5 million barrels a day (up to 45% of the USA East Coast’s supply of diesel, gasoline and jet fuel). As a direct consequence, critical assets like fuel pipelines has been shut down and pump prices can be increased in the USA.
If they have been targeted, are your critical infrastructure safe against a cyber attack?
Are you too big to fall? Think twice
Ransomware attacks are not new to critical infrastructures, but they are now a growing tendency. Recently, Norsk Hydro, an aluminium maker was also attacked, prompting the switching of aluminium related factories; according to the company [1] “Production lines had stopped at some of its 170 plants. Other facilities were switching from computer to manual operations.” Final financial impact exceeded $71 million dollars. Moreover, a recent intrusion on a natural gas compression factory forced a two-days shut down of its complete pipeline [2].
In this scenario, EPES are not, by any means, free of threats. They face daily attempts of intrusion (and possibly unnoticed long-term campaigns of intrusion like it happened in the infamous Ukrainian incident[3] with an attack that started at least 6 months in advance) and even dedicated malware like the CRASHOVERRIDE malware family [4].
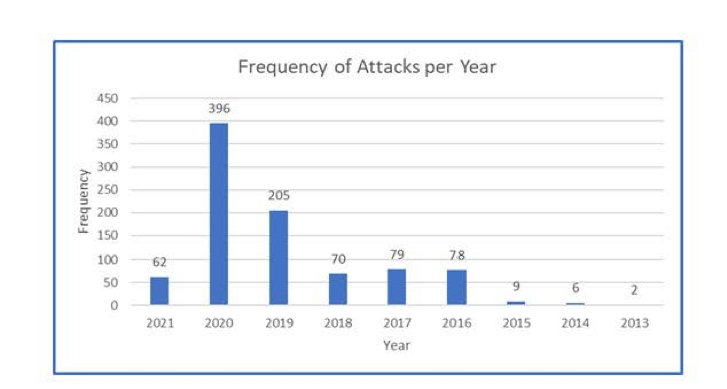
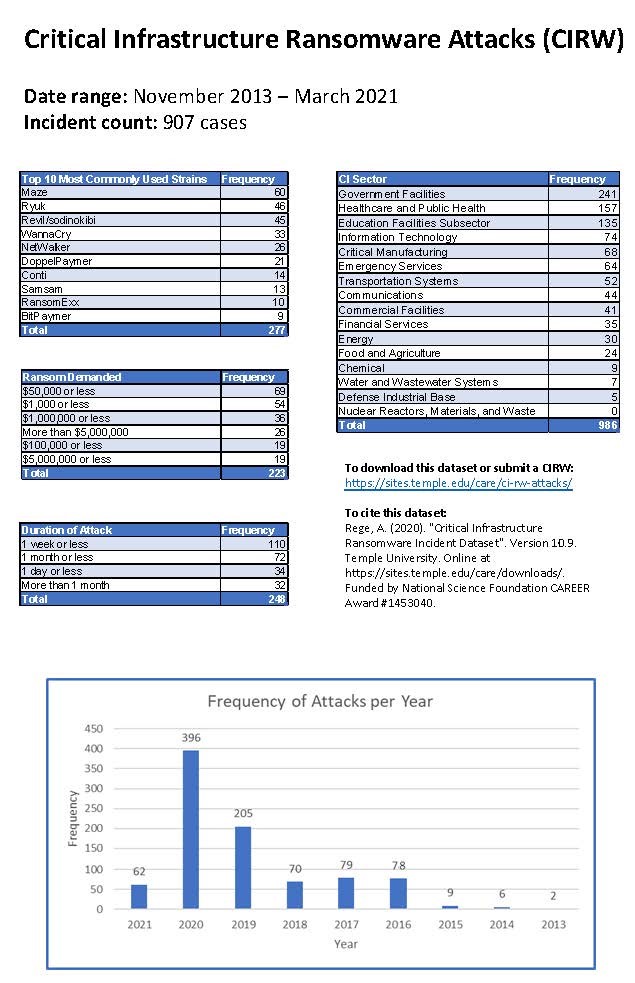
According to Temple university dataset of Critical Infrastructures Ransomware Attacks (CIRWAs) [5] in the past seven years there has been 907 attacks on critical infrastructures with half of them occurring since 2019. No less than thirty of these attacks were targeted on the Energy sector.
So, what is next for us? Critical infrastructures are in the bull´s eye of malware organizations (no more a jerk in a dark room, but hundreds of jerks in their particular silicon valley ‘s). We need to be ready with new and imaginative ways of addressing threats. Projects like PHOENIX are the academic and the industry approach to the problem, but we clearly need to put more focus on cyber protection of our critical infrastructures. Who knows who can be next?
References
- [https://news.microsoft.com/transform/hackers-hit-norsk-hydro-ransomware-company-responded-transparency/]
- [https://us-cert.cisa.gov/ncas/alerts/aa20-049a].
- [https://www.globalsign.com/en/blog/cyber-autopsy-series-ukranian-power-grid-attack-makes-history]
- [https://us-cert.cisa.gov/ics/alerts/ICS-ALERT-17-206-01].
- [https://sites.temple.edu/care/ci-rw-attacks/]












