Improved efficiency of secure CTI sharing in PHOENIX platform

The main goal of the PHOENIX project is to build a cyber-shield armour to European Electric Power Energy System (EPES), securing such infrastructures against unsolicited and solicited malicious behaviours. To this end, the PHOENIX platform devises the Secure and Persistent Communication (SPC) layer which enables the secure and efficient exchange of information, describing the security status of EPES infrastructures.
More specifically, the SPC layer given the growing concern about data security and privacy develops a blockchain-enabled secure CTI sharing platform that considers the data protection regulations particularly the General Data Protection Regulation (GDPR) [1] while leveraging a private permissioned blockchain for security properties. To achieve this, the preliminary prototype of SPC layer extended the technological capacity of the TAXII framework with blockchain and publish-subscribe middle-ware, addressing the inherited deficiencies of the platform including lack of support for the data authenticity in the database and event-driven architecture. The rationale behind selecting the TAXII framework as the basis of PHOENIX’s CTI sharing platform was to address interoperability issues between public and private sectors since the TAXII standard is deemed as one of the most prominent solutions for transporting cybersecurity information.
The effectiveness of the CTI sharing platform depends not only upon forming a trusted relationship between a publisher and a consumer but also highly relies on the reliability of shared information.
Therefore, a security expert before acting upon received threat information first would assure the trustworthiness of a CTI publisher and then would ensure that the integrity of the information has been preserved throughout the sharing process. For this reason, the CTI sharing framework of the SPC layer only allows the authenticated and authorised producers to publish CTI. To achieve the latter principle which was not supported in the preliminary prototype of SPC layer but was added to the final implementation, a publisher stores the hash of information in blockchain which would be later utilised by a consumer to validate the integrity of a received CTI. Thereby, the enhanced CTI sharing platform benefits from the tamper-proof logs, transparency and traceability features of blockchain while minimizing the performance loss arising from the interaction with blockchain by recording only the essential data (i.e. CTI’s hash) on blockchains and storing the actual CTI data in a database.
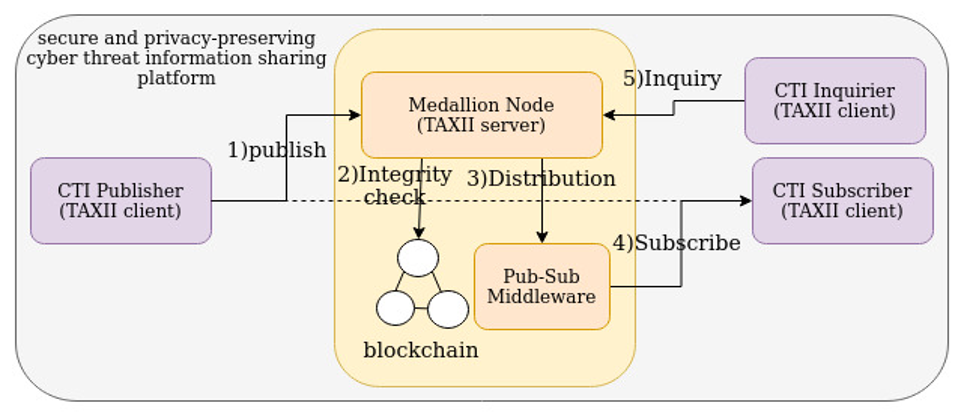
As illustrated in figure 1, the SPC’s CTI sharing framework is composed of three key components: TAXII client, TAXII server (i.e. Medallion node) and pub-sub middleware and operates as follows: A TAXII client with the producer role publishes new threat information to the TAXII server where CTI is stored in the database. Additionally, the client writes the hash of CTI in the private blockchain where only authorised partners can execute transactions. Despite several advantages of storing threat information in the private blockchain, this approach has some shortfalls such as lower throughput and immutable records compared to the database. Thereby, the PHOENIX sharing platform leverages the database and the blockchain simultaneously to achieve better performance while protecting the data integrity against cyber attacks. Upon reception of a CTI object, the server retrieves the respective hash from the blockchain and checks it against the hash value calculated using the received CTI. If there is a mismatch, the server discards the object otherwise it persists in the database. Next, the server distributes the threat information to the interested clients via the pub-sub module. A client who subscribes to a certain type of CTI would receive the relevant data from the server. Similar to the server, the client validates the integrity of the received CTI using the hash value stored in the blockchain. The server also provides a specific CTI object in response to the client’s request. In this case, the TAXII server retrieves the queried threat information from the database and sends it back to the client. The client examines the authenticity of the received data using the hash value in the blockchain.
The new implementation of the CTI sharing platform in the PHOENIX SPC layer has been developed during fall 2021 and spring 2022. It is described in more detail in the D2.4 deliverable and is part of the demonstrations in the upcoming review.
References:
[1] Tokarski, M. Protection of Individuals in the light of EU Regulation 2016/679 on the Protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of such Data.Safety & Defense2020,6, 63–74.












