How Do We Comprehensively Understand Complex Attacks on Smart Grid Environments?

With regards to the ongoing transformation of power grids into intelligent, automated systems – called smart grids – equipped with several assets for managing power flux and energy balance, such as measurement devices (Phasor Measurement Units, Smart Meters), actuators (circuit breakers, disconnectors) and network equipment (gateways, control nodes), the question of how to comprehensively perceive and understand complex, multi-staged attacks on smart grids is gaining increasingly more significance. Even through relatively few malware implementations caused severe physical damage to smart grid systems in the past, the number of highly sophisticated, orchestrated cyber-physical attacks has increased during the last decade, making detection and the implementation of countermeasures upmost critical for the safe operation of smart grids. Thus, a structured and coherent understanding of the threats is vital for developing and designing appropriate defense strategies.
To identify and understand the vulnerabilities and threats that the smart grid systems are increasingly exposed to, it is crucial to analyze the targeted and its related infrastructure, with special emphasis on the information and communication technology (ICT) domain. Subsequently, the main features of smart grid ICT infrastructure are the predominance of machine-to-machine communication (high predictability), homogeneity in assets (ideal environment for malware spreading), differences in network requirements across several device types (conflicting goals), physical access to field devices by non-trusted parties (weak access management), long life span of installed field devices (longevity of vulnerabilities), pre-authorization of field devices to local servers (stored authentication information), and the requirement for remote upgrade support (remote access possibility) [1]. Most of the inherent weaknesses can be addressed by following adequate security policies and guidelines, such as regular security updates, strict user management, strong password policy, modern detection software, network segmentation with distinct objectives, restriction of remote access, strict firewall rules, decentralization of critical services, dimensioning hardware for future software updates and user education. However, the effective utilization of those actions as well as ensuring data integrity, confidentiality and availability require a great understanding of the potential threat surface endangering the critical infrastructures.
Several concepts and models of complex attack procedure life-cycles were developed to tackle the aforementioned challenges as they provide a structured and comprehensive methodology. For instance, the Cyber-Kill-Chain [3] method including Advanced Persistent Threats [2] and other threat modeling techniques like STRIDE and DREAD can provide sufficient coverage of the aforementioned subject. Based on this, a generic model for multiple stages in the cyber-attack life-cycle is presented in Figure 1. It illustrates the complexity of such attacks, their range, impact and, foremost, the dynamics and interactions within the procedure and attack phases. Starting with the access phase to critical resources, directly or remotely, the attacker tries to evaluate its privileges for further propagation activity. In case of sufficient access points, discovery activities are triggered to identify new targets and vulnerabilities. Once new targets have been identified, the attacker propagates to the new host by exploiting the prior detected vulnerabilities. A successful, large-scale attack requires sufficient access to compromised resources to enable coordinated actions and orchestration. Thus, after access to the new host system is gained, the infection and escalation of privileges is triggered to establish external command & control (C&C) functionality. Finally, covert and conceal operations are performed to hide tracks and traces of the attack.
Our mission in PHOENIX is to provide an armor for the European energy and power systems against complex attacks and sophisticated intruders. For this purpose, we develop a platform that is capable of comprehending the current cyber-physical situation and its implications, the attack evolution, the quality of the collected information, the attack impact on critical assets, the attacker behavior throughout an incident and possible future developments to carry out appropriate mitigation, countermeasures and recovery plans.
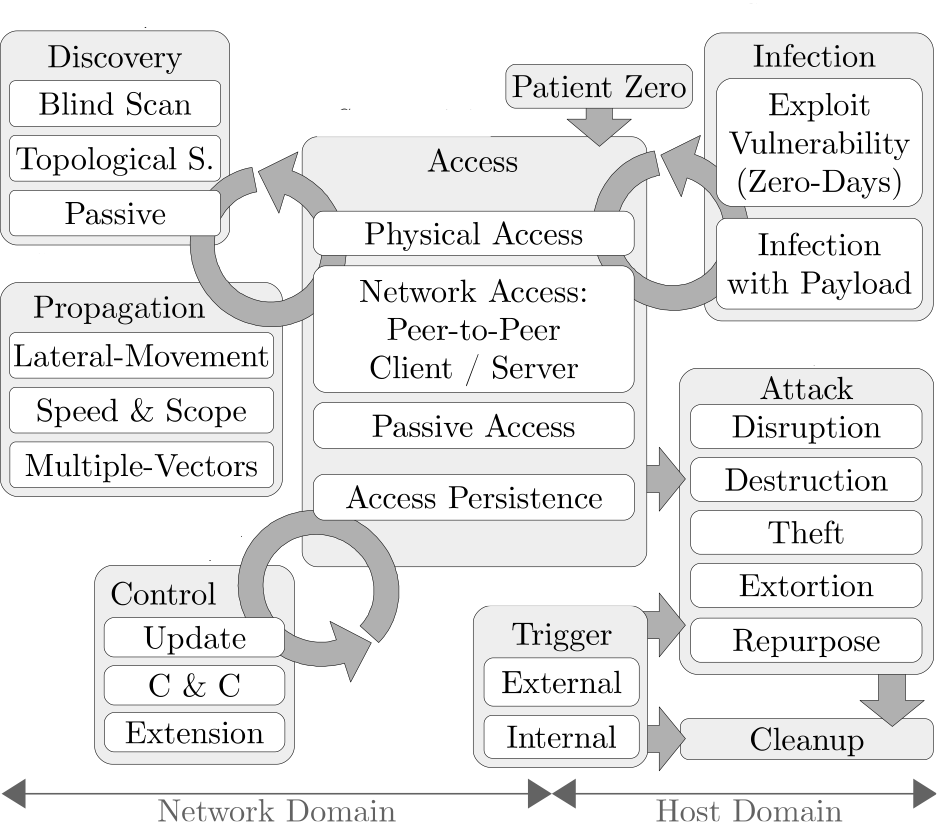
Figure 1: Generic Stages of Malware-based Cyber Attacks [1].
References
| [1] | Tanja Zseby, Joachim Fabini, Gernot Vormayr Peter Eder-Neuhauser, 2017, “Cyber attack models for smart grid environments”, Sustainable Energy, Grids and Networks, 10-29. |
| [2] | Leyla Bilge, Gavin O’Gorman, Seán Kiernan, and Martin Lee Olivier Thonnard, 2012, “Industrial espionage and targeted attacks: understanding the characteristics of an escalating threat”, Intrusions, and Defenses (RAID’12) In Proceedings of the 15th international conference on Research in Attacks, Ed. Berlin, Heidelberg: Springer-Verlag, 64–85. |
| [3] | Lockheed Martin Corporation, 2015, “Seven Ways to Apply the Cyber Kill Chainwith a Threat Intelligence Platform”, White Paper PIRA# CMK201507003. |












