Evaluating the security of electricity infrastructures

The electrical grid constitutes of legacy systems that were built with no security in mind. As we move towards the Industry 4.0 area though a high-degree of automation and connectivity provides: 1) fast and flexible configuration and updates as well as 2) easier maintenance and handling of misconfigurations and operational errors. Even though considerations are present about the security implications of the Industry 4.0 area in the electrical grid, electricity stakeholders deem their infrastructures as secure since they are isolated and allow no external connections. In this article we elaborate on these considerations and indicate that external connections are not the only security risk for electrical utilities.
Starting with a brief introduction on the electrical grid, it constitutes by 4 subsystems:
- the production, that comprises by electricity stations to produce energy from different sources (e.g. lignite, petroleum, natural gas)
- the transmission, that handles the distribution of energy to entire cities or neighborhoods
- the distribution, that handles the dispatch of energy to the households or factory buildings
- the consumption, that concerns the usage of electricity in the households or factory buildings
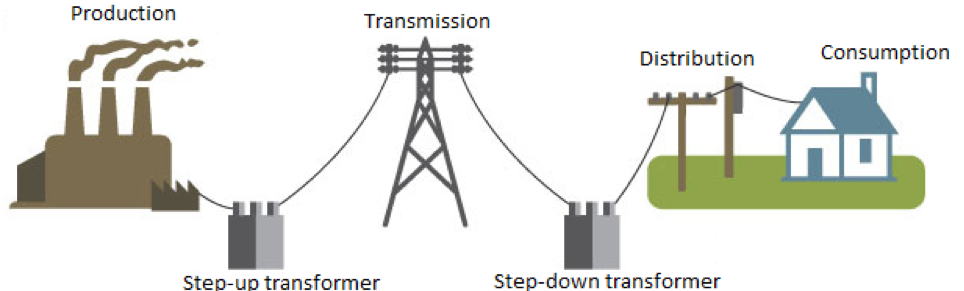
As depicted by the above figure the grid is a chain, where each subsystem is vital for its operation. However, certain subsystem components of the grid are more critical than others as their replacement has great impact in the business continuity (e.g. budget loss and restoration effort). For example, the electricity stations are more critical to a utility company than the power transmission lines. Hence, utility stakeholders focus on protecting the critical subsystems, such as the production subsystem through the belief that no external nor remote connections should be allowed. In practice though this belief does not hold as the production subsystem constitutes by several third-party components that the utility company has no control nor can maintain without supply chain personnel. Hence, such personnel need to be given physical or remote access to the utility to install and update the components, to act upon operational errors as well as perform configuration changes. All these actions require dedicated software or drivers that are usually located in external drives or can be accessed by the supply chain personnel through the enterprise environment. In every scenario the system is no longer isolated, leaving open communication ports or interfaces that can be leveraged by adversaries with malicious intents. Furthermore, as the configuration of electricity components uses default or common passwords, an adversary can accordingly obtain control the functionality of the industrial process causing catastrophic consequences.
A second belief of utility stakeholders is that in the rare scenario than an adversary gains access to any of the subsystems, no harm can be caused as the underlying communications and exchanged commands cannot be interpreted. This belief does not hold as well since over the last years the interpretation of proprietary communication protocols was facilitated by dedicated tools and techniques. Specific examples are available command interpreters for the DNP3 protocol that is used for control and data communication among SCADA system components as well as the protocol dissectors and parsers for the IEC 104 electricity station protocol, following the IEC60870-5-104 standard. Given the availability of protocol handling commands, the protocols are no longer restricted and proprietary. This allows unauthorized entities to not only understand the commands exchanged by in electricity systems, but also reply by sending malicious commands to them.
PPC has 98 electricity stations distributed around the area of Greece [1]. These stations are used for energy production through lignite, petroleum, natural gas, but also through alternative energy forms as wind, sun or geothermal. Moreover, they were designed to operate continuously without interruption for large time spans (~ 30 years). As the security risks are increasing with exponential rate, the PHOENIX consortium aims to develop a cyber-resilience strategy, in order to detect incidents that could potentially cause harm to its electricity stations as well as protect the stations with mitigation measures for both well-known and zero-day security threats.
[1] https://www.dei.gr/en/i-dei/i-etairia/tomeis-drastiriotitas/paragwgi/analutikos-xartis-stathmwn












