Dissecting the Crashoverride malware framework

As advanced malicious activity on critical infrastructures are rapidly increasing in frequency and sophistication, the PHOENIX research & development project will aim to provide an impregnable cyber-shield armour for the future European energy systems.
This blog will focus on Crashoverride, a malware that utilized ICS-specific protocols to control and disrupt grid functionality by paralyzing a single transmission substation in the capital of Ukraine, Kiev, December 17th, 2016. Today and about five years later, the event is still highly relevant when it comes to implementing cybersecurity in the power grid of tomorrow. The purpose of this blog is to briefly understand Crashoverride in more depth and provide some mitigation strategies against similar attacks.
The first technical report of Industroyer was released in 2017 by ESET in Europe [1], followed by publication under the name Crashoverride by Dragos in US [2]. The main components of the malware framework are depicted in Figure 1 and is further explained below. The highly modular framework was discovered by means of reverse engineering and malware analysis. Crashoverride is said to be dangerous in the sense of being vendor independent, as well as its ability to leverage the knowledge of grid operations [2].
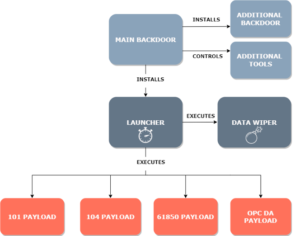
Figure 1: Crashoverride malware framework
The Main Backdoor is the core component of the autonomous malware with the main objective to install and orchestrate malicious components and tools. As backdoors akin, a remote command & control (C2) connection is used to establish two-way communication over TLS or HTTPS. This way the attackers could remotely control every component of the malware if necessary and what’s more, the C2 servers are using onion routing (ToR) software, thus making it very hard if not impossible to trace back [1]. The Data Wiper is the component responsible to make system recovery difficult by deleting registry keys and otherwise vandalize the victim system environment by editing, rewriting, or deleting content and vendor-specific files. The Data Wiper can also terminate critical processes to cripple the system and subsequently cause a system shutdown [3]. Another malware component is the Launcher, which is derived, installed, and initiated by the Main Backdoor. The Launcher appears on the victim system as a separate executable file that is responsible for initiating the Data Wiper or execute any of the custom-made ICS payloads. The payloads are regular Windows DLL files, as further explained in ESET’s technical report [1].
Furthermore, the authentic industrial protocols that were utilized by the ICS custom payloads are IEC 101, 104, 61850 and OPC DA. The IEC 101 is a protocol that enables remote and telecontrol tasks, whereas the IEC 104 protocol extends IEC 101 and enables communication between control station and substation via TCP/IP. The IEC 61850 is a bundle of standard protocols that enables communication for intelligent electronic devices (IEDs) at electrical substations. The OPC DA protocol is used to interface devices like HMI, SCADA and ERP/MES systems.
security teams should have a clear understanding of the IEC 104, IEC 61850, DNP3 and similar industrial protocols. From a cybersecurity perspective it is imperative to know where and how they are used within the system environment. One indicator of compromise to look for is an increased usage and network flow against the established baselines. For instance, the OPC protocol was used by Crashoverride to scan all devices on the network, thus generating more traffic than usual. Furthermore, the malware investigators and security experts underline that it’s not sufficient to only have ICS anti-virus, air-gapped networks, or unidirectional firewalls. Human defenders are required. A more exhaustive list of Crashoverride defense recommendations is given in [2].
Ultimately, PHOENIX will aim to create a fully distributed Pan-European incident’s information sharing platform (I2SP) between CIRTs and CERTs across the countries. This platform will allow the creation of mitigation plans and countermeasures, along with existing threat and malware patterns, incorporating methods for blockchain, distributed ledger technology (DLT) and deep machine learning, as well as extensive logging mechanisms to deal with anomalous activities and offer a host-based protection level against malicious malware.
In the end, Crashoverride was an ambitious attack that in fact was considered as a failure or even a large-scale test by some security experts. Nonetheless, the attackers WILL learn from their mistakes and continue to develop a malware framework that, sooner or later, will attempt to impact the electric power and utilities in a similar manner. Therefore, it is in the hands of the PHOENIX project to tackle this problem through synergy and breed forth a safe, secure, and reliable European smart grid that is ready for the cyber-attacks of the future.
References:
- https://www.welivesecurity.com/wp-content/uploads/2017/06/Win32_Industroyer.pdf
- https://www.dragos.com/wp-content/uploads/CrashOverride-01.pdf
- https://www.dragos.com/wp-content/uploads/CRASHOVERRIDE2018.pdf
- https://www.dragos.com/wp-content/uploads/CRASHOVERRIDE.pdf












