Applying Privacy-by-Conception in Cybersecurity
Originally published on cyberethicslab.com
Alessio Bianchini, Elena Sartini and Luigi Briguglio from CyberEthics Lab., partner of the PHOENIX consortium [1], are the authors of the article “Applying Privacy-by-Conception in Cybersecurity”, published in ERCIM News no.126 Special Theme “Privacy Preserving Computation” (July 2021) [2].
In this article, the authors describe how the PHOENIX project is approaching the design and implementation of cyber-shield systems to protect assets and networks of the Electrical Power and Energy System (EPES), where fundamental dimensions (including privacy and data protection, ethics and social concerns) must also be considered.
Specifically, two relevant assets have been defined:
- a methodology (the PRESS Framework) has been defined, in order to reconcile technology development activities with privacy, ethics, security and societal concerns;
- a blockchain-based privacy protection enforcement (PPE) component that implements mechanisms able to provide better protection for personal data in compliance with the GDPR [3].
To enable a harmonic dialogue between technical components and legal/ethical issues, CyberEthics Lab. has drafted a comprehensive tool for all the companies involved in the project, which follows four steps: 1) definition of the conceptual framework in which the technological solution was intended to be placed and with which the desired solution should find a way to dialogue in harmony; 2) identification (i.e. logical deduction from the conceptual framework) of the compliance requirements for the final design of the technological solution; 3) juxtaposition of the requirements identified with potential concerns/threats which might have originated from their non-compliance, alongside guidelines and policies that aim to avoid (or at least mitigate) the occurrence of threats/concerns; 4) definition of a checklist with the translation in technical language of the “conceptual” requirements, relevant concerns/threats and policies, alongside the most apt technical components. The latter is a valuable tool, to be shared between technical teams and auditors, for monitoring the appropriate evolution of the technology implementation, enacting the compliance assessment, and reporting tests and evidence for qualifying the delivered artefact.
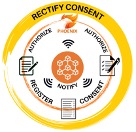 To ensure that data from the EPES are organised and managed in such a way that organisations can meet enterprise business needs along with legal and governmental regulations, a privacy protection enforcement mechanism provides the following features (see Figure 1): 1) express consent required to process data; 2) the right to rectify given consent; 3) more and clearer information about processing; 4) the right to notification if data is processed/compromised; 5) immutable data access log.
To ensure that data from the EPES are organised and managed in such a way that organisations can meet enterprise business needs along with legal and governmental regulations, a privacy protection enforcement mechanism provides the following features (see Figure 1): 1) express consent required to process data; 2) the right to rectify given consent; 3) more and clearer information about processing; 4) the right to notification if data is processed/compromised; 5) immutable data access log.
The PHOENIX activities are still ongoing, however, further details on these relevant assets are available in the article.












