Privacy and Data Protection, Ethics, Social and Security Framework Analysis within the Energy Sector

Today, technologies make many aspects of our lives interconnected and interdependent. In this scenario, the development of new technological solutions should consist not only in the analysis of the best technical components, but also in the understanding of the ethics, regulatory, and security contexts in which the solution will be implemented. By adhering to this dual approach, researchers can prove that technological progress occurs in harmony with other instances of human life.
What has been described above is the approach adopted by the PHOENIX project, a HORIZON 2020 EU Funded project, whose main objective is to develop a cyber-shield able to protect the electrical smart grid infrastructure from cyber threats. This infrastructure is considered critical by the European Union, and therefore merits a system such as the one designed in PHOENIX that early detects and avoids (or, in the worst-case scenario, mitigate) threats or attacks directed at it.
At CyberEthics Lab., we have translated this new research approach into the following 4-step– methodology applicable in all sectors.
- Creation of a clear picture of the conceptual framework in which the IT solution will be placed and with which the solution should find a way to dialogue in harmony.
- Further analysis aimed at the identification (i.e. the logical deduction from the conceptual framework) of the compliance requirements for the final design of the IT solution.
- Juxtaposition of the requirements identified with potential concerns/threats which might originated from their non-compliance, alongside with guidelines and policies aiming at avoiding (or at least mitigating) the occurrence of the identified threats/concerns.
- Definition of a checklist composed of the translation in technical language of the “conceptual” requirements, plus the relevant concerns/threats and policies, alongside the most apt technical components. The latter is a valuable tool, to be shared between technical teams and auditors, for monitoring the appropriate evolution of the technology implementation, enacting the compliance assessment, and reporting tests and evidences for qualifying the delivered artefact.
In the PHOENIX case specifically, the ideas behind the method described above have been included in deliverable D4.1 – PRESS Analysis Framework (a public deliverable and that will be published on the project’s website). Therein, after having clarified the specific sector in which the project is conducting its research activities and defined the ethics requirements (i.e. D10.1, D10.6, D10.8) as well as from the general privacy policies and guidelines (i.e. D1.1 and D1.3), the analysis carried out shows three “pillars” (privacy and data protection, ethics and social concerns, and security elements). For each of them, the document describes (i) the relevant conceptual framework, (ii) the methodology for assessing the technology according to pre-defined requirements derived from the framework analysed, (iii) potential concerns able to impact the requirements identified. The final chapter of the document provides the PHOENIX project with a practical set of compliance rules and governance policies (a sort of practical “handbook”) designed to properly apply ethics, legal, and social principles during the research activity for each requirement identified and described in the three pillars. These compliance rules and governance policies will be then implemented throughout a DevSecOps[1]process occurring across the entire project lifecycle. In accordance with the definition of the DevSecOps process, which aims to embed security practices from the inception of technological solutions, the technical requirements will be made into a checklist. This last is to be used during the test and assessment, and should provide evidence of the delivered artefact’s compliance to the PRESS Framework.
The process overview and the outcomes of the PRESS Framework are illustrated in the following figure.
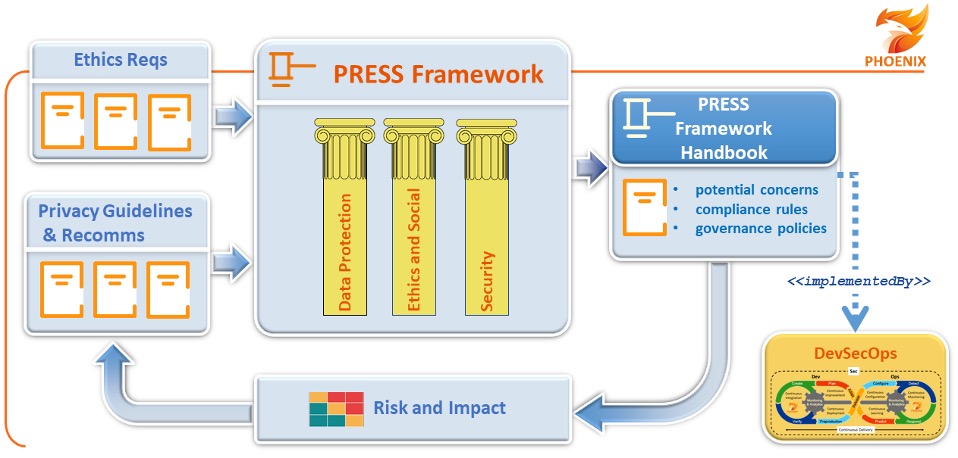
As can be seen, the PHOENIX project has been a means for us to develop a unified method allows developers to that incorporates ethics requirements, privacy guidelines and recommendations, and results from multidimensional risk assessments. Hence, the name PRESS, an acronym deriving from the key words PRivacy, Ethics, Security and Societal. We believe that the advantage of a similar framework is to ensure data protection thanks to omni-comprehensive guidelines for the implementation phase of technological solutions. Such solutions would thus be able to utilise the best technical components while adhering to the appropriate and proportional the compliance requirements identified.
To achieve such a result in other domains, it is indispensable for professionals with different backgrounds (legal, ethicists, technical etc.) to work closely together and to find common ground for describing phenomena and requirements and identifying ethics and legal concerns. This kind of cooperation, which finds fertile ground in EU-funded research projects, can provoke a shift in the DevSecOps mindset: from legal and regulatory nuisance, compliance activities can come to define better technologies and provide them a greater chance of adoption and long-term use.












